MSP security – discover and remediate MFA exposure with one click automation
When it comes to managing Microsoft 365 and other SaaS apps for your customers, there’s lots of security best practices to put in place – from Multi-factor authentication (MFA), strong passwords, consistent policy settings, and more. But with every native admin console or center that your team must hop through, it becomes even more challenging to get the information you need to take action. Not only is this a problem for your customers – it can put your business at risk too. Getting ahead on security, like discovering and remediating MFA exposure, is even more critical today with increased work-from-home arrangements during the pandemic.
In this article we cover the importance of one critical security layer – MFA, as it can be a vital first-line of defense against an assortment of security exposure problems. As an old adage goes, a warrior’s armor is only useful if they remember to wear it to the battlefield. Below, we illustrate how to easily get a handle on MFA exposure by putting the automation capabilities of SkyKick’s Cloud Manager to use.
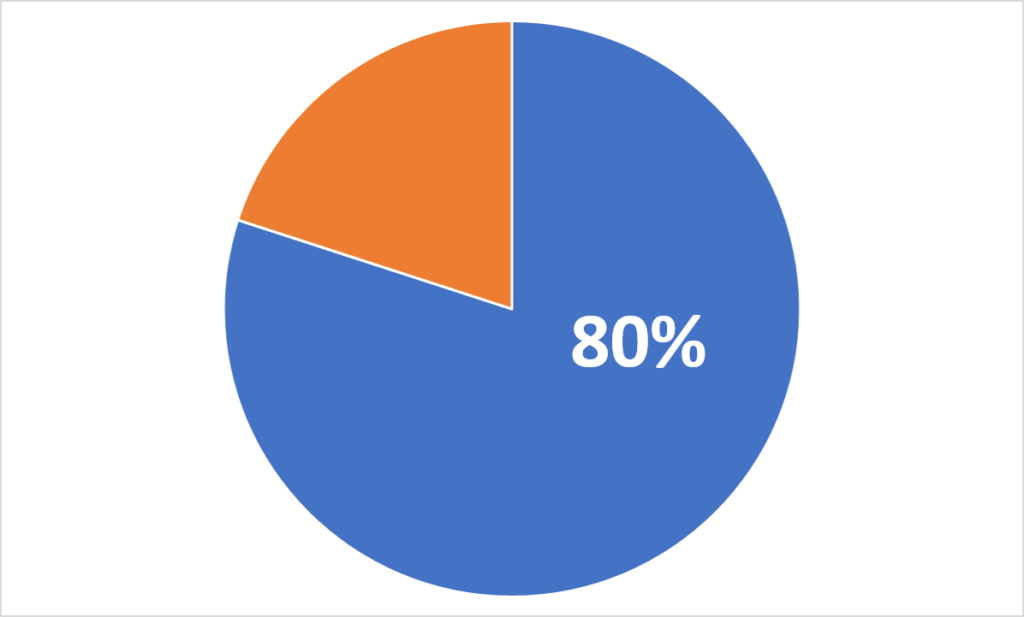
Over 80% of breaches from hacking involve brute force or the use of lost or stolen credentials
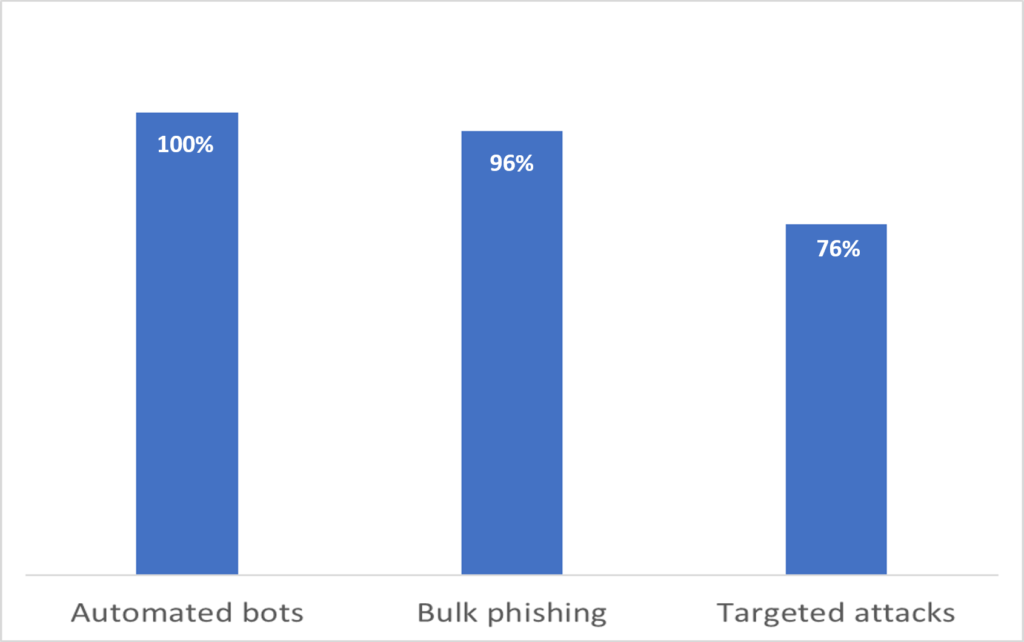
According to the Verizon 2020 Data Breach Investigations Report, over 80% of breaches from hacking involve brute force or use of lost or stolen credentials. MFA can all but eliminate this risk by requiring a second form of authentication. In fact, recent Google research reports that an SMS code sent to a recovery phone number helped block 100% of automated bots, 96% of bulk phishing attacks, and 76% of targeted attacks. And since a lot of the increased remote work could be expected to be over unsecured home and public networks, now is a perfect time to accelerate MFA adoption.
| Breaches from hacking using force or lost/stolen credentials | Effectiveness of SMS code against various attacks |
 |
 |
The MSP challenge of managing security across customers
Most partners already ensuring that MFA is enabled for all customers when configuring their Microsoft 365 tenants. But if someone has disabled this critical security feature on the tenant or for any user for whatever reason, it can put your customer at extreme risk. What’s more, getting visibility into every end user at every customer for both analysis and remediation can be overwhelming and time-intensive.
Separately accessing each customer tenant is time consuming and introduces risk due to multiple logins, especially if using shared credentials. The inefficiency continues as Microsoft 365 admin centers must be navigated one customer at a time to identify security gaps. If gaps are found, accurate, and consistent remediation must then be performed one customer at a time, requiring more time – and introducing the potential for errors.
How Cloud Manager helps
It is this and other key MSP cloud management challenges that SkyKick Cloud Manager was developed to solve. In fact, Cloud Manager provides a single pane of glass for your entire team to efficiently and securely manage customers across multiple cloud services, portals, and even hybrid configurations.
So when it comes to critical security initiatives like MFA, you can run a single command across all customers to get a report of any user who has multifactor authentication (MFA) disabled. Importantly, you can also immediately remediate with built-in automation, which can be run from a codeless interface or a PowerShell console built for the cloud.
While taking control of MFA is a good start, stronger security of course is a journey and involves much more. Cloud Manager is your ally in this pursuit. Persistent token-based connectivity enables single scripts to run across cross-customer for monitoring, discovery, and reporting, for remediation of issues, and to standardize configurations across customers. Every action that is taken in Cloud Manager is automatically recorded in the Activity log for improved security, compliance, and reporting.
See Cloud Manager in action
Watch this < 4-minute video to see how easy it is to run a cross-customer report from Cloud Manager without having to log into and out of multiple tenants, navigate multiple admin portals, or even know an ounce of PowerShell. To do so, just…
- Select and run the cross-customer command from the no-code Command Center
- Review the PowerShell output
- Immediately remediate gaps from same no-code interface
Cloud Manager: Perform cross-customer MFA check from SkyKick on Vimeo.
Try it for yourself
Cross-customer MFA management is just one example of all that Cloud Manager makes possible for your cloud business. There’s lots of ways to use the product to apply standardized security policies and settings, and ensure your customers are compliant.
Sign up for a free 30-day trial of Cloud Manager by logging into SkyKick.com, selecting Cloud Manager in the left navigation, and following the trial setup process. Then, you can walk through the steps for performing a cross-customer check using these instructions.



